Using website data to predict and avoid a hacker attack

Published 2023-03-14
Summary - When you notice an increase/decrease in website traffic, unusual visitors and traffic to your login page, and/or that your website has become slow or unresponsive, do not dismiss these patterns; they could be an indication of an impending hacker attack.
37,000 websites are hacked daily.
The cost of data breaches will increase to $2.1 trillion globally in 2019. This figure is expected to rise to $6 trillion by 2021.
The costs of hacking include damage and destruction of data, stolen money, lost productivity, theft of intellectual property, theft of personal and financial data, embezzlement, fraud, post-attack disruption to the normal course of business, forensic investigation, restoration/deletion of hacked data and systems, and reputational harm.
According to Fortune.com, 66% of businesses attacked by hackers weren’t confident they could recover.
Thankfully there are online resources that provide valuable insight into activity on your website. Within your Google Analytics and Google Search console, for example, you can uncover data that provides early warning signs that hackers are targeting your website. This information is also available if you have access to server analytics - such as Webalizer or AWStats, in your cPanel.
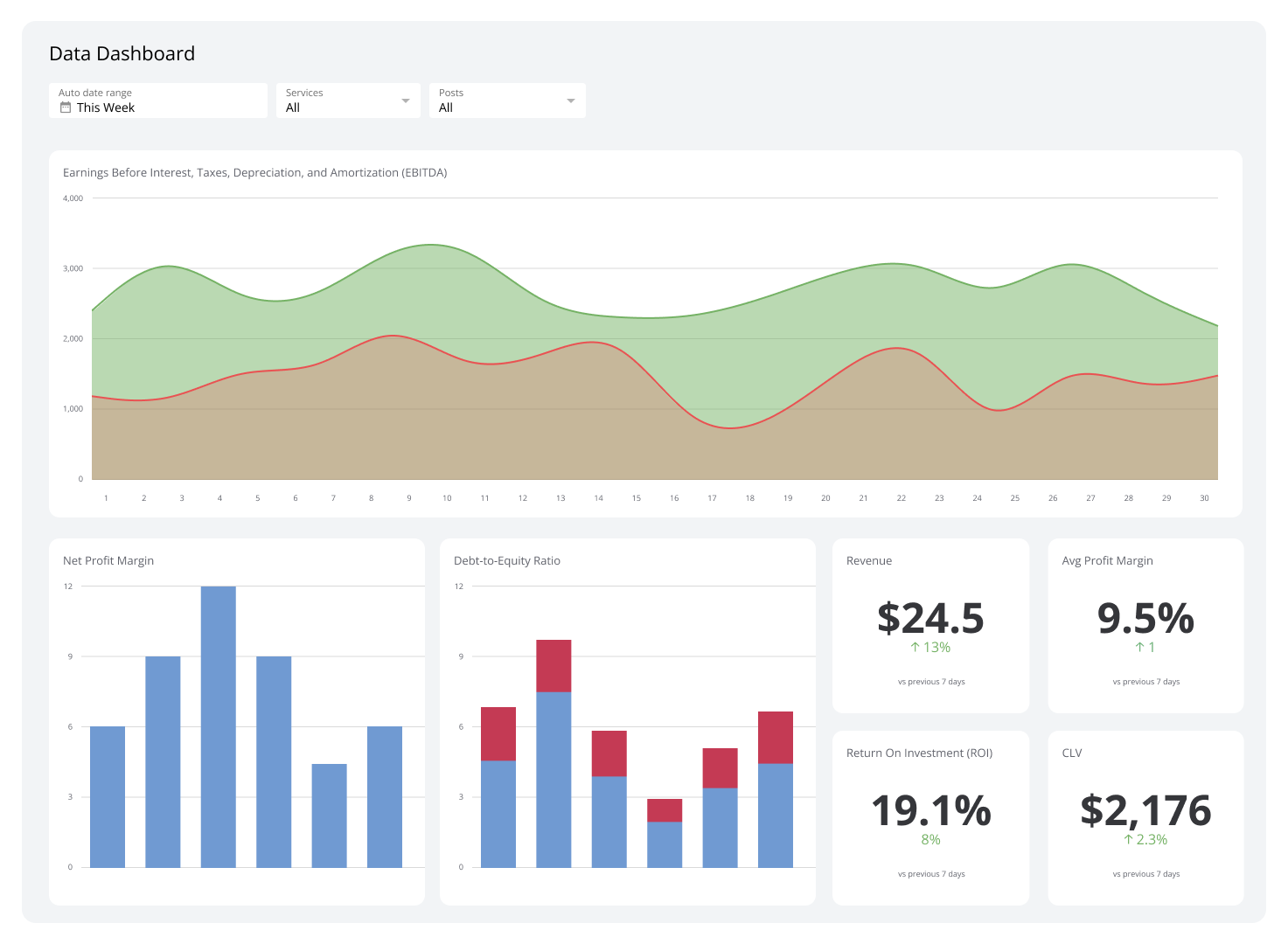
Website Traffic
If you regularly monitor your website analytics, you have a good understanding of where your traffic originates from. These are likely the geographic locations you are targeting with your marketing efforts. However, once hackers have targeted your website, your analytics will report an increase traffic coming from unexpected or unwanted regions.
Most nefarious website attacks originate from only a handful of countries. According to a report ABC
It is important to note that in contrast to an increase in website traffic, it is possible for a sharp decrease to indicate you've been hacked; as well. The loss of visitors can be attributed to:
- Fear. If visitors see anything on your website that piques their suspicion or threatens their security, they will leave immediately.
- Google. If Google blacklists you, the search engine will issue warnings about your website within their search results. Obviously if this happens, people will not click through.
- Impatience. If your website has crashed or is slow at delivering web pages, people will "bounce"
Prevention Strategy
If you have noticed that you are being bombarded with visits from a specific country, or simply want to deny access to your website from one or more countries, you can use the .htaccess file to accomplish this.
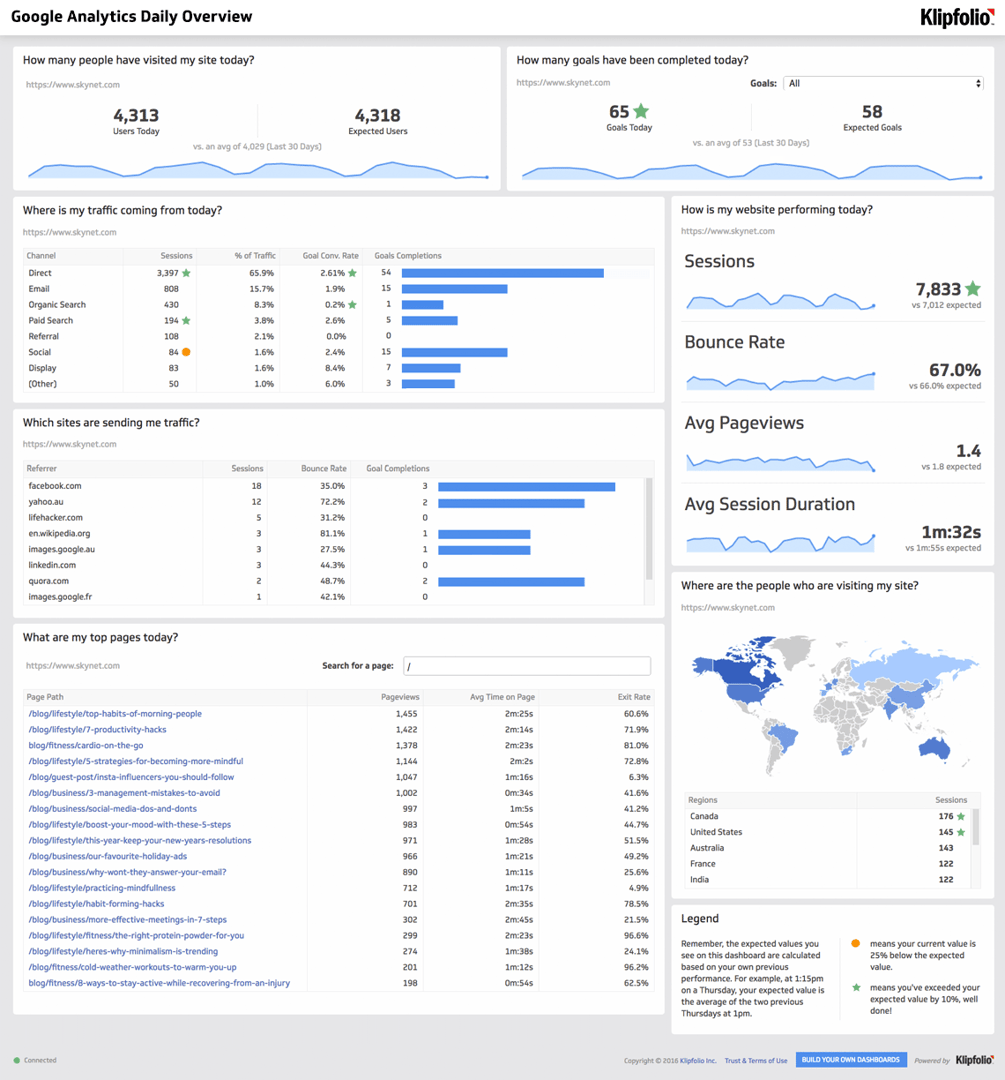
Login Page Visitors
The most common website hacking technique is an SQL Injection attack. Hackers often gain access to a website, content management system, or application by inserting SQL code into web forms; such as login fields. An SQL Injection attack can permit hackers to spoof identity, tamper, destroy or disclose data, void eCommerce transactions, or make the website, CMS, or app unavailable.
If a hacker believes a website is vulnerable, there are login strings available all over the Internet to help them gain access to weak systems. In this case you’re analytics platform will be reporting an abnormal amount of traffic to your login page. It is really that simple.
According to IBM and Ponemon’s Institute’s Cost of a Data Breach study, the average cost to repair a SQL Injection attack is $157 per user.
Another frighteningly simple process which can be employed against poorly designed applications or content management frameworks provides access to the Admin back end and is called an Authorization Bypass. The target for this attack is often a weak login page.
User authentication plays an integral role in the security of web applications. Based upon a login name and password, an application is able to establish the user's identity and assign them specific privileges to the system. The Authorization Bypass hack tricks the system into believing the hacker is already authenticated and thus provides access to internal pages. This kind of attack is not necessarily attributed to lax security in the Operating System or server software, but rather on how securely stored and complex your passwords are, as well as how easy it is for the attacker to reach your server.
Prevention Strategy
If you are noticing an increase in the number of visits to your website's login page, it could be an indication that hackers are attempting to gain access to your database by using SQL code injection or an Authorization Bypass. To deter these types of attacks:
- In place of admin.php (for example) as your admin login page, name it something less revealing.
- Whitelisted IP addresses ensure that only your team can access website administrative areas. Restrict your admin panels to only authorized IP’s so malicious users don’t gain access.
Generally speaking, Web applications only ask for a username and password at the login page and then permit authorized users unfettered access to the website, without any further security checks. This approach (mistakenly) assumes that the only way to access configuration pages is through the login page. Time and again it has been demonstrated that hackers are able to go directly to configuration pages, easily bypassing authentication. To prevent this type of simple bypass, it is necessary to implement security checks to authenticate users on every page, rather than assuming that if a user has reached a given page they must have permission.
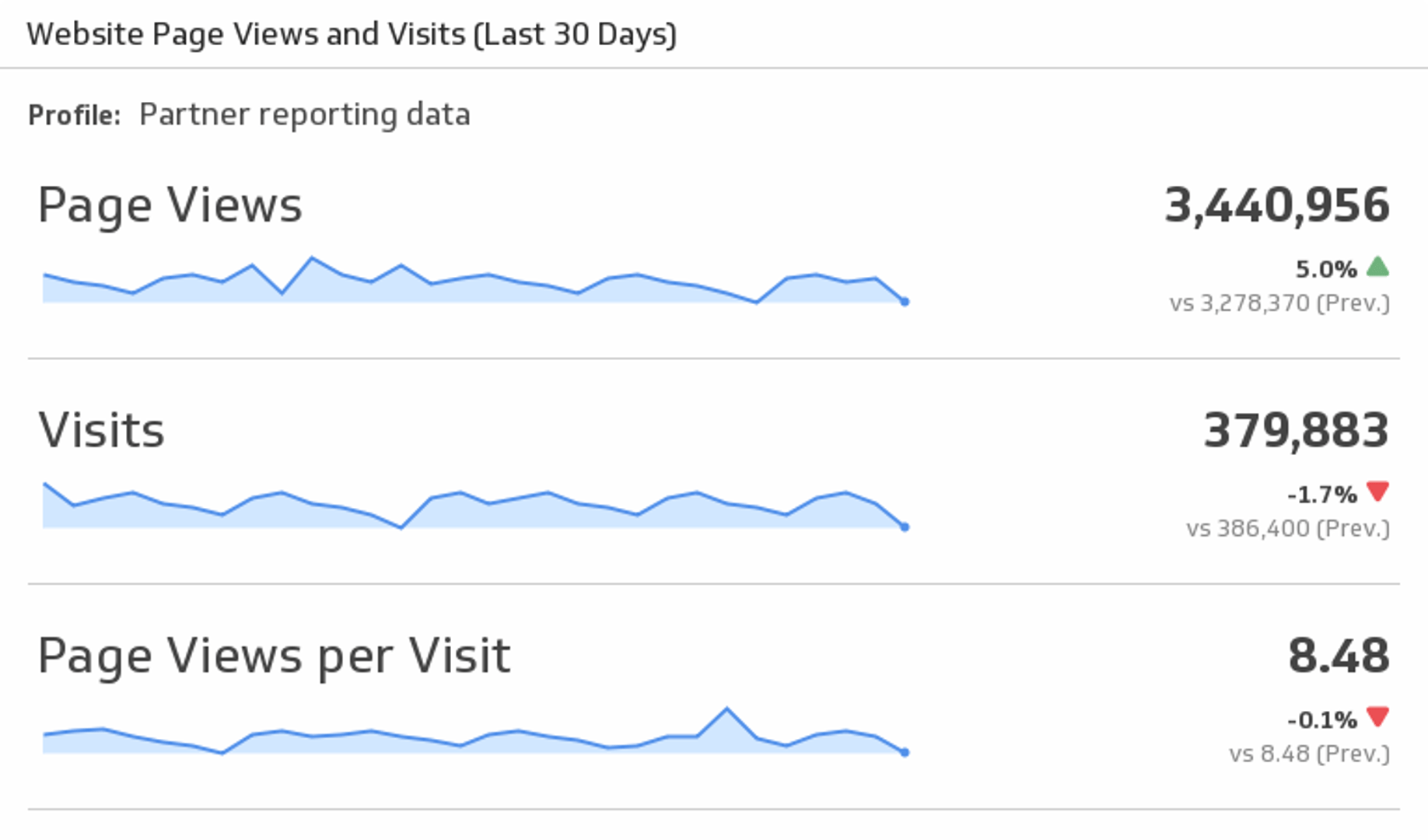
Slow or Unresponsive Website
An early indication of a hacked website could be slow loading webpages or displayed generic 500/503 server errors. This is especially true if you know the number of real users of your website has not increased significantly, but your website is operating more slowly than usual.
In this instance, the hacker may be using your website server to store an enormous number of files; like shareware or illegal information. Making matters worse, they may run these files on your server thereby increasing the usage and reducing performance. When you consider that the average attention span of today’s digital consumer has decreased to 8 seconds, slow websites are bad for business.
Prevention Strategy
Check for changes to core files. Do not limit your search to functions.php, index.php, and 404.php files. Do a thorough review, paying especially close attention to the dates that files were last updated. In most instances, you will notice an unusual date in comparison to other files. Overwrite the hacked documents with unaffected duplicates. This exercise reinforces the need to maintain a current backup copy of your website.
In Summary
Many people mistakenly believe only large businesses and corporations are at risk of a hacker attack. The truth is, the number of cyber attacks on small businesses have intensified. In fact, 43% of all cyber attacks are aimed directly against small businesses, and - much more frighteningly, these attacks cause 60% of affected SMBs to go out of business within six months.
To ensure that your business does not become one of these statistics, it is important to avoid the mindset that you “have nothing worth stealing”. Fundamentally, this is untrue. As a business owner, you have customer and employee information; and, this sensitive data is valuable to a hacker.
When you notice an increase/decrease in website traffic, unusual visitors and traffic to your login page, and/or that your website has become slow or unresponsive, do not dismiss these patterns; they could be an indication of an impending hacker attack.
About the Author
Garry Brownrigg is the Founder & CEO of QuickSilk, a secure SaaS content management system that provides simple and affordable CMS solutions for small to medium size enterprises.